If you spend enough time around VMware Cloud on AWS, you will likely end up managing multiple organizations. Many customers isolate Production in its own org. In my team’s case, I have 3 – our Production customer-facing demo environment, our Test environment where engineers can create and destroy SDDCs at will, and an early access environment.
You can use Groups to make your administrative life easier. To create a group, click Add Groups under Identity & Access Management > Groups.
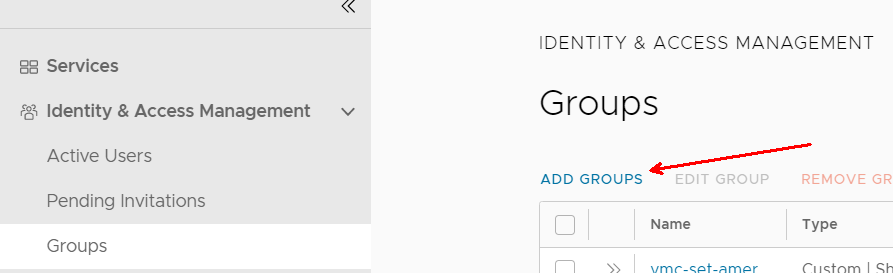
If you are federated, you can pick a group from your federated domain. In this case, we are creating a new group.
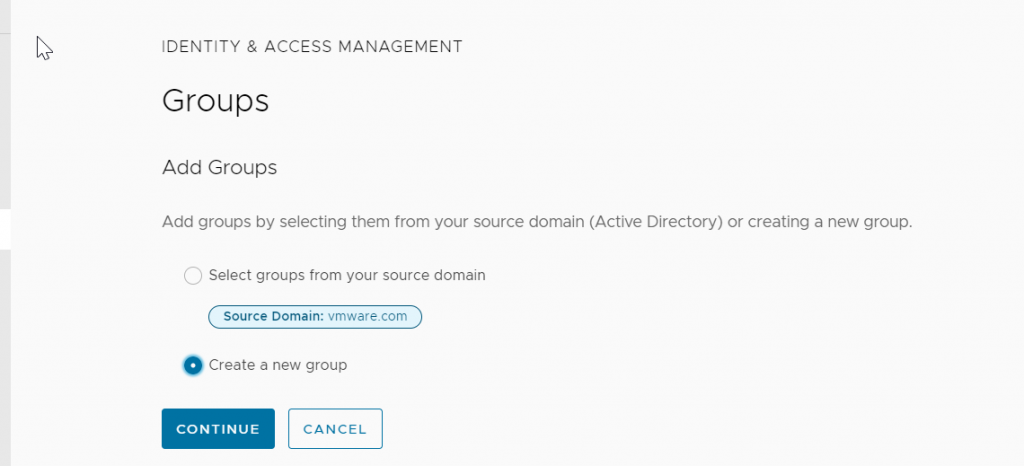
First we name the group and give it a description. Then we click on Add Organizations to share the group.
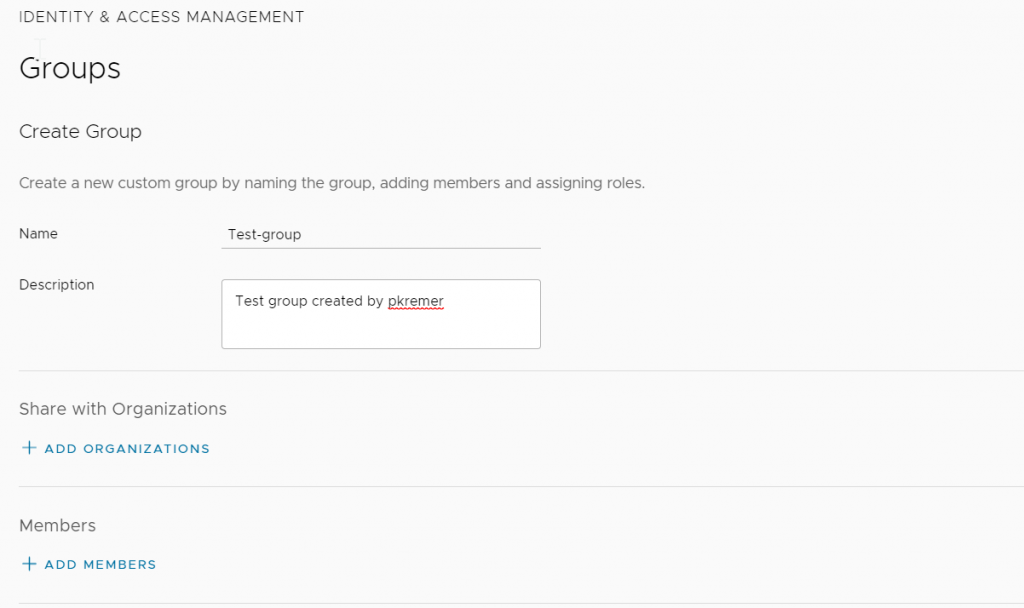
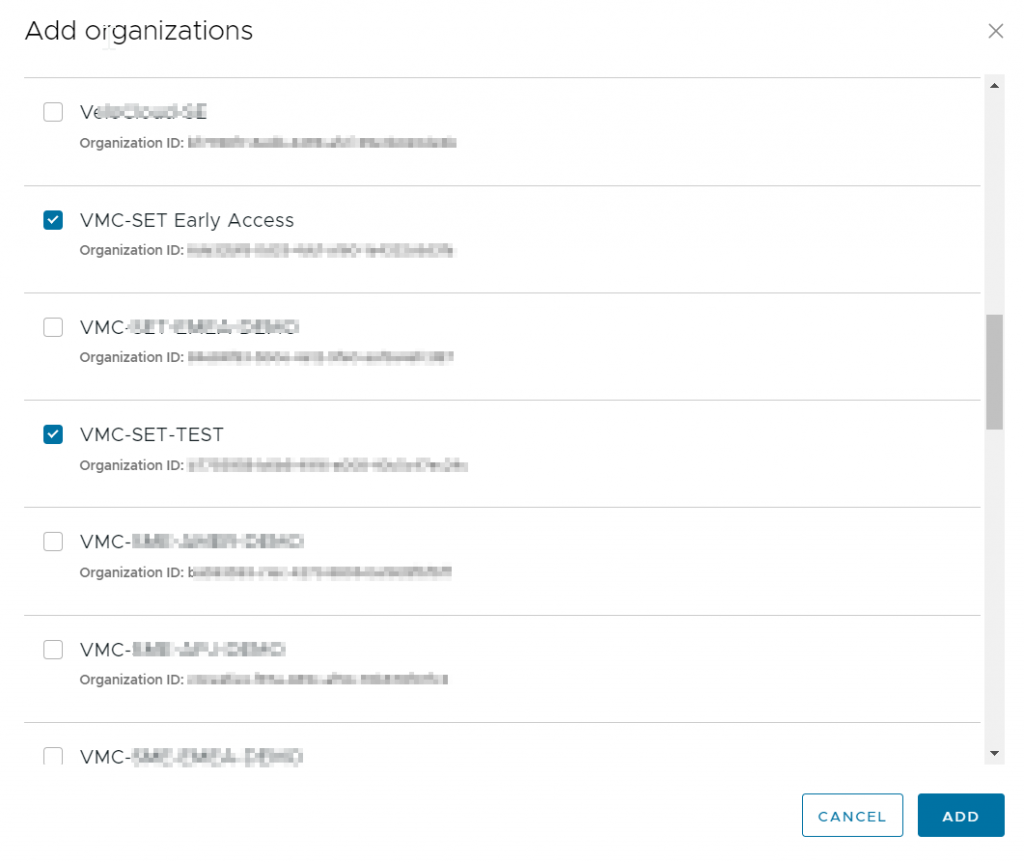
You can enter a specific OrgID if you know it. You can also scroll through all of the orgs that your currently logged in user has access to.
I check the boxes for the Early Access and the Test org, then click Add
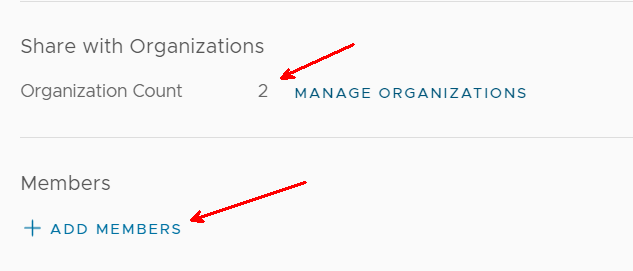
This group show as being shared with 2 organizations. I click on Add Members
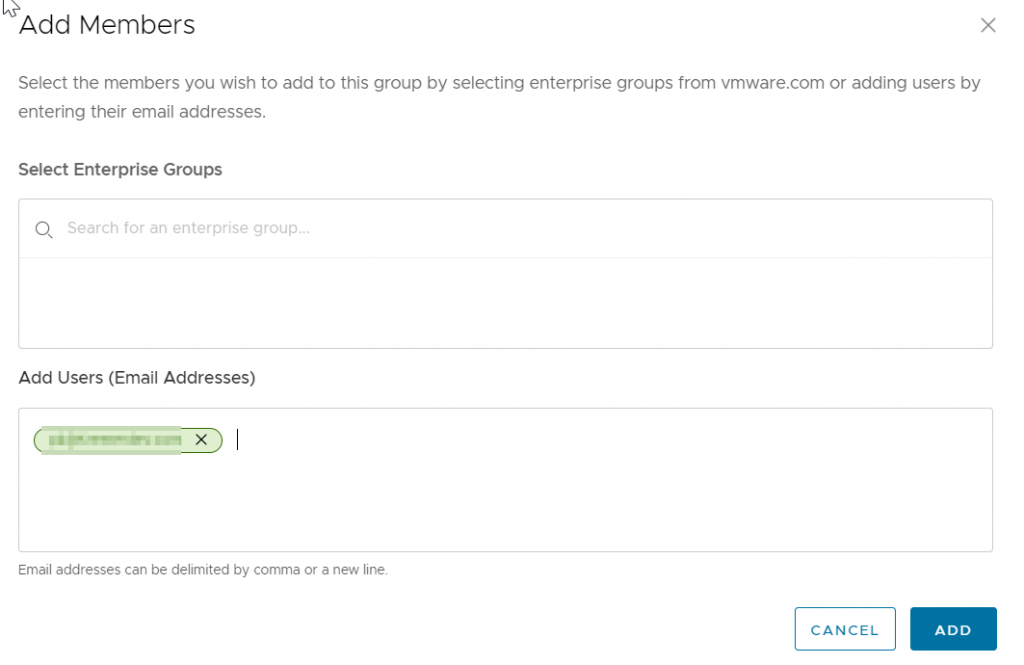
I could add groups of users from my federation. Instead, I add a single user by email address, then click Add.
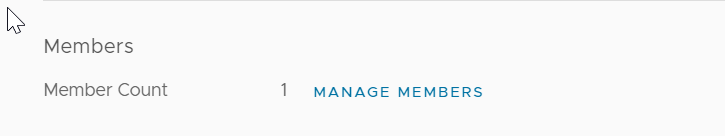
Now my group has one member in it.
I need to assign the group a set of roles – I want to grant Delete Restricted access to VMware Cloud on AWS.
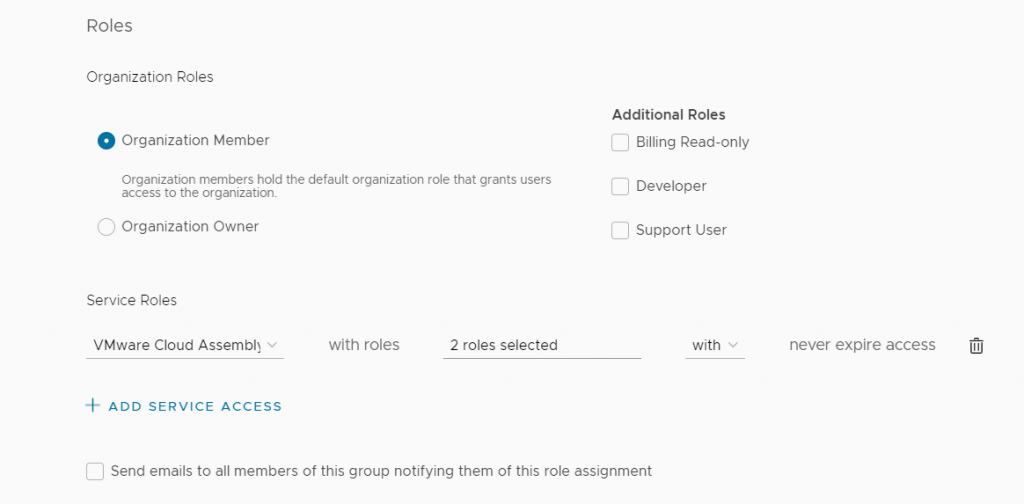
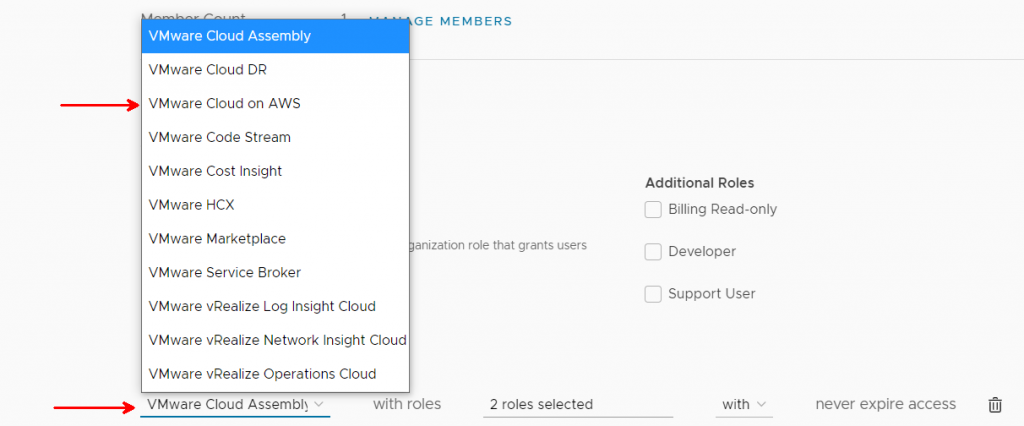
I select VMware Cloud on AWS from the dropdown.
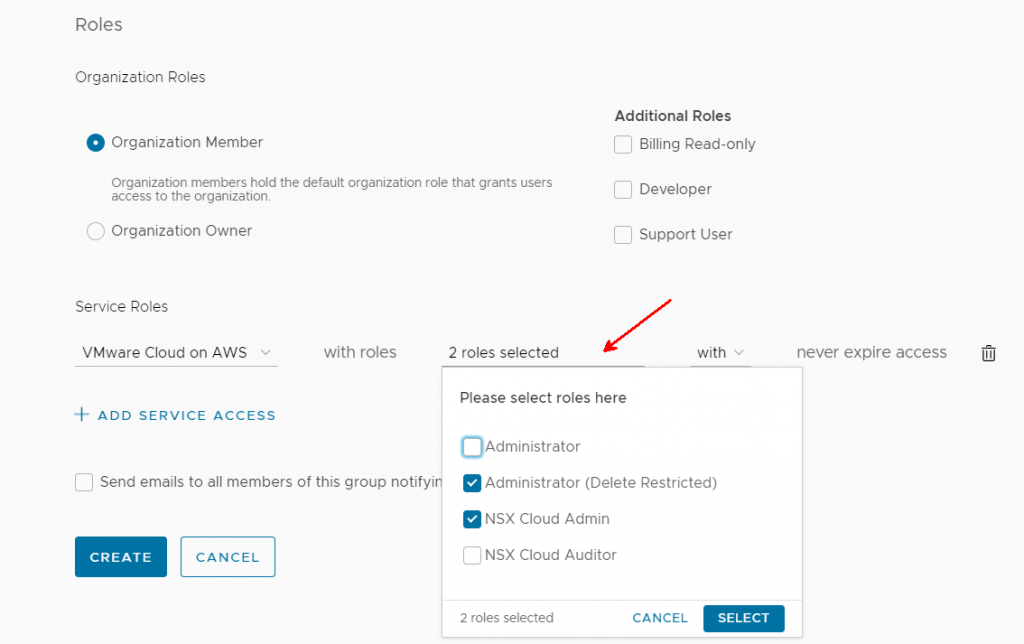
I check the boxes for Administrator (Delete Restricted) and NSX Cloud Admin.
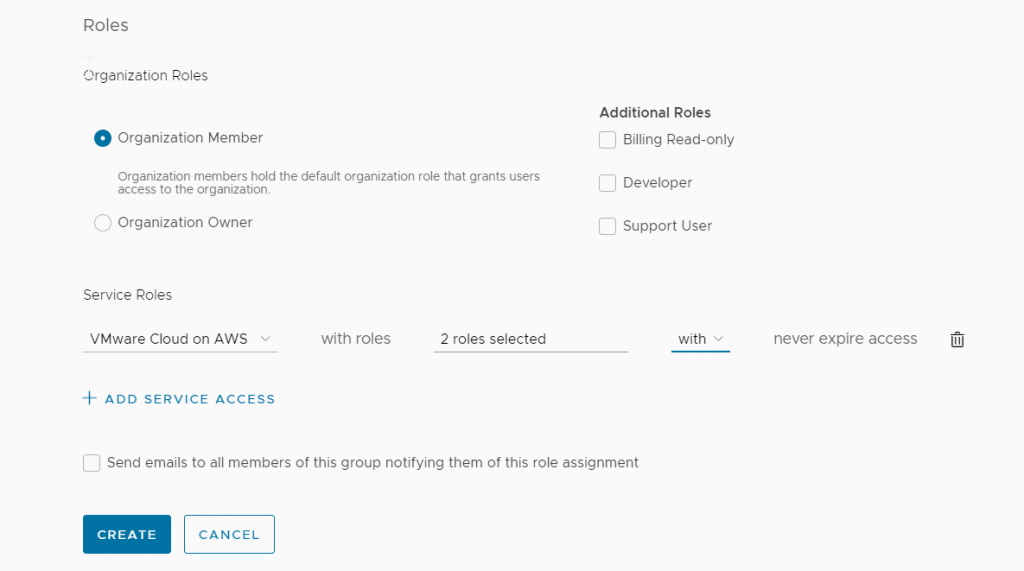
I click Create.
Now I edit the user that I added to the group.
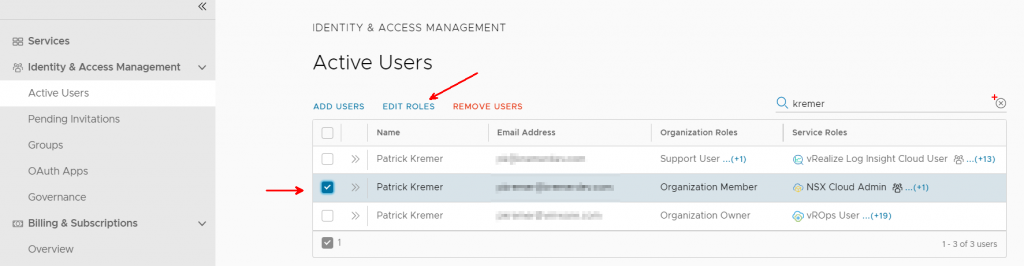
You can see the user has the specific roles added to the group. I cannot change them, I cannot delete the roles granted by the group. However, I could add new roles.
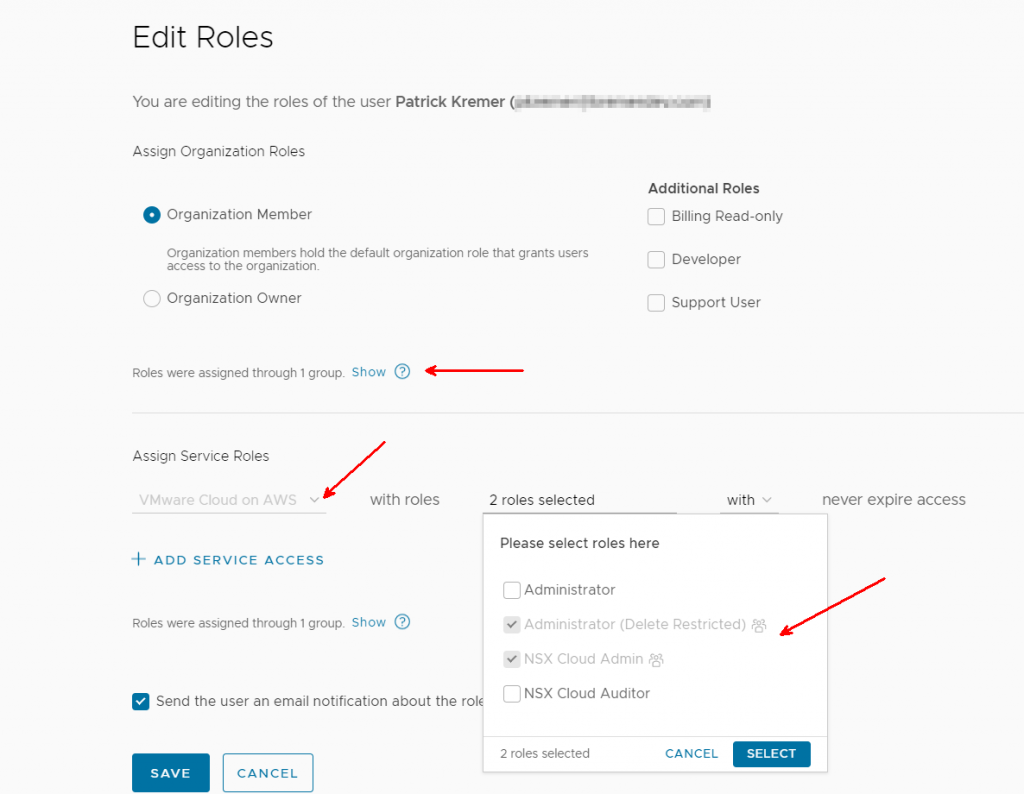
I switch to the Test organization but the group is not there. You have to explicitly add a shared group. I click Add Groups.

I select Import groups and click Next.
I click the down carat to see a list of organizations that have shared a group to this organization.
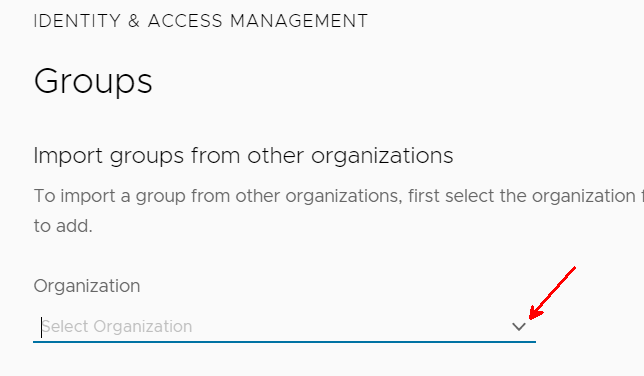
I pick my Production demo org.

I pick the Test-group.
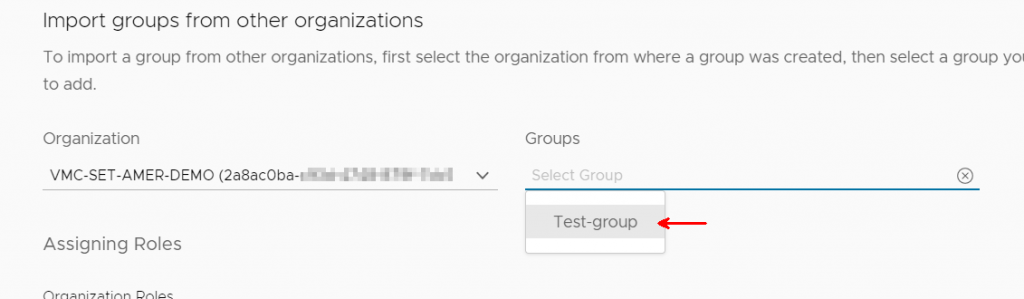
Only the group members are shared – the roles themselves are independent of the group. This allows me to have a group of Delete Restricted folks in the Production demo lab, but allow that same set of people rights to create and destroy SDDCs in the Test org.
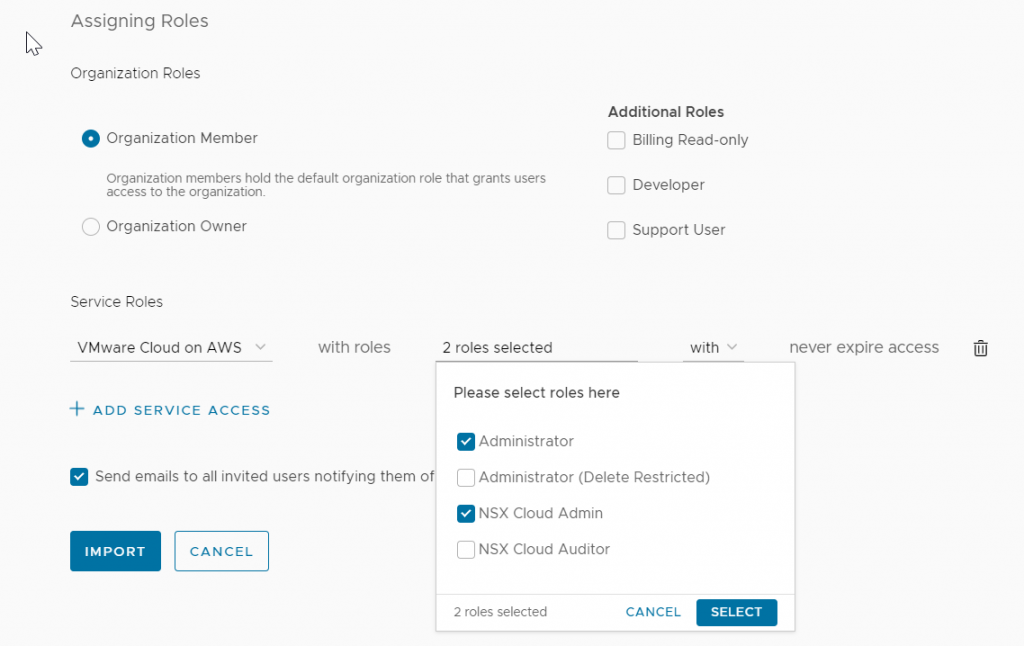
Now any time I add a user to the Test-group in the Production Demo org, they will be granted access to the Test org.

Python Client for VMC on AWS - Part I - User Management -
[…] permissions or group permissions. The VMC on AWS Portal has great features for sharing groups across organizations if you want to use them. However, for various reasons detailed in the sync roles blog post, you may […]
SDDC Import/Export for VMware Cloud on AWS – Part VII – Role Sync Feature -
[…] VMware Cloud Services portal has great features for sharing roles across organizations. However, there are situations where you may not want to use it. You might have corporate security […]