I recently needed to replace the default self-signed certificate with a fully trusted SSL cert on my VEBA appliance. The VEBA OVA installer does let you specify a certificate at install time. But if you need to replace an existing cert, whether it’s a public cert or the self-signed default cert, you can follow this procedure.
A free way to get a fully trusted certificate is via Let’s Encrypt. Certbot is the utility you use to interact with the Let’s Encrypt service. I use these instructions to get the Certbot utility on my laptop:
https://certbot.eff.org/lets-encrypt/windows-other
I download the Certbot installer for Windows here:
https://dl.eff.org/certbot-beta-installer-win32.exe
My existing VEBA appliance has a URL of vmcveba02.kremercloud.com. I tell Certbot to issue me a certificate for that URL using DNS as validation that I am the owner of the domain.
certbot certonly --manual -d vmcveba02.kremercloud.com --preferred-challenges dnsNote: Certbot fully supports wildcard certificates – *.kremercloud.com is valid input for the -d switch.
Certbot instructs me to add a specific TXT record to my DNS. The command prompt sits at ‘Presss Enter to Continue’ while I make the DNS change.
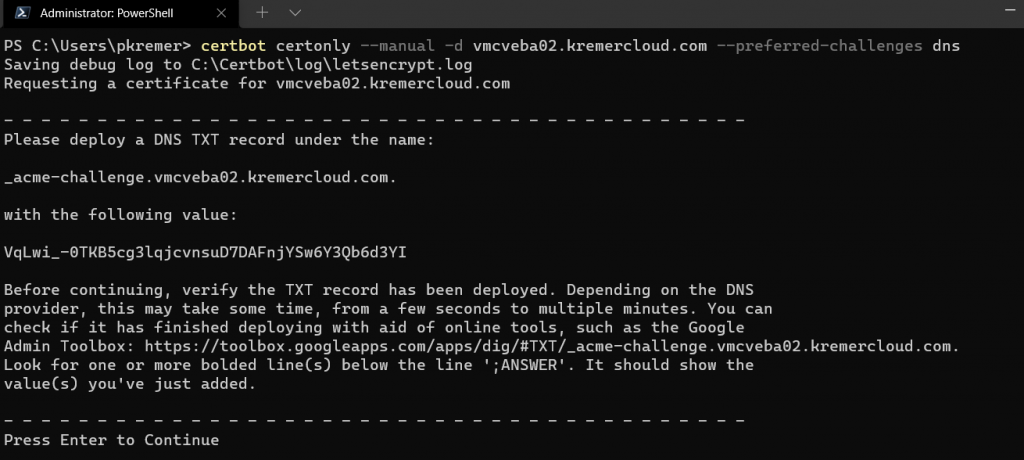
My domain is hosted in AWS – I configure the TXT record as show in Route 53.
I return to the command window and press Enter. DNS is validated and the certificate is issued.
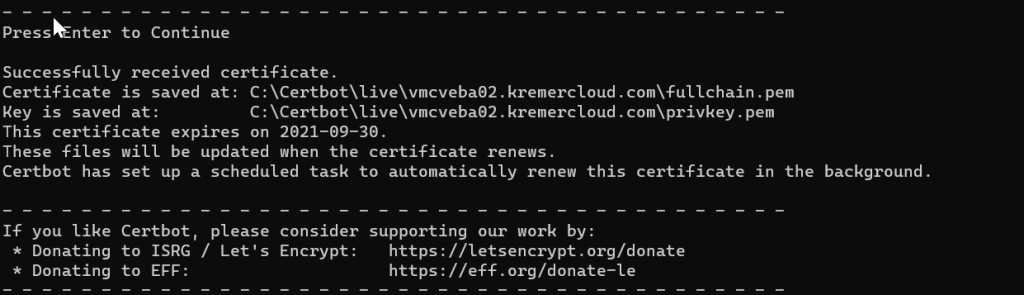
As shown in the output, the certificate is written to C:\certbot\live. I use WinSCP to copy the entire vmcveba02.kremercloud.com folder to /root/config
I replace the Event Router secret with the new certificate.
cd /root/config/vmcveba02.kremercloud.com
kubectl -n vmware-system delete secret eventrouter-tls
kubectl -n vmware-system create secret tls eventrouter-tls --key privkey.pem --cert fullchain.pemThen I replace the Contour secret – Contour provides endpoints like /stats and /events.
kubectl -n contour-external delete secret default-cert
kubectl -n contour-external create secret tls default-cert --key privkey.pem --cert fullchain.pem The new certificate is now fully deployed.

VMware Event Broker Appliance – Part VIII – Building a new PowerCLI Function - Preparation -
[…] the previous post, we discussed Let’s Encrypt public certificates in VEBA. In the next few posts, we will […]