This is the first post in a blog series on the Python Client for VMC on AWS (PyVMC).
I recently blogged about a new feature in the SDDC Import/Export for VMware Cloud on AWS Fling – the ability to sync roles across organizations. You have 2 choices when managing users – individual permissions or group permissions. The VMC on AWS Portal has great features for sharing groups across organizations if you want to use them. However, for various reasons detailed in the sync roles blog post, you may have to manage permissions individually.
Regardless of whether you choose to manage by group or individually, commands that have been added to the PyVMC Fling in v1.4 can help make management simpler.
show-csp-groups
This command shows you all of the available user groups in your organization.
C:\git\Flings\python-client-for-vmware-cloud-on-aws [master ≡ +0 ~1 -0 !]> python .\pyVMC.py show-csp-groups
+--------------------------------------+---------------------+------------+------------+
| ID | Name | Group Type | User Count |
+--------------------------------------+---------------------+------------+------------+
| c13ae3cf-xxxx-xxxx-xxxx-xxxxxxxxxxxx | cmbu-guests | USER_GROUP | 0 |
| 3d6f43a8-xxxx-xxxx-xxxx-xxxxxxxxxxxx | vmc-set-amer-member | USER_GROUP | 4 |
| 857ebe60-xxxx-xxxx-xxxx-xxxxxxxxxxxx | vmc-set-amer-owner | USER_GROUP | 18 |
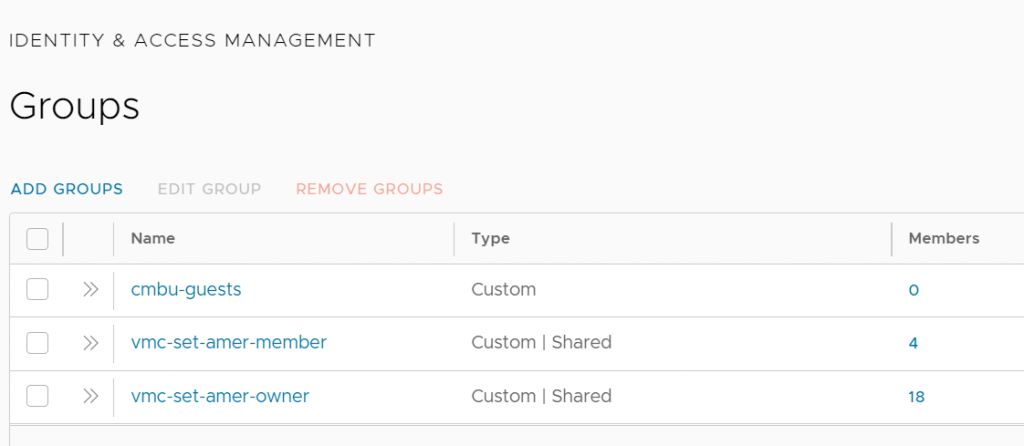
+--------------------------------------+---------------------+------------+------------+Here is what the groups look like in the CSP UI.
show-csp-group-members
Once you have the group ID from the show-csp-groups command, you can pass it as an argument to show-csp-group-members to see all users in the group.
C:\git\Flings\python-client-for-vmware-cloud-on-aws [master ≡ +0 ~1 -0 !]> python .\pyVMC.py show-csp-group-members 3d6f43a8-218b-xxxx-xxxx-xxxxxxxxxxxx
+----------------------+------------+-----------+----------------------+-------------------------------------------------+
| Username | First Name | Last Name | Email | userId |
+----------------------+------------+-----------+----------------------+-------------------------------------------------+
| jsxxxxxxx@vmware.com | John | Sxxxxxxx | jsxxxxxxx@vmware.com | vmware.com:b6abd79b-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
| msxxxxx@vmware.com | Michael | Sxxxxxx | msxxxxx@vmware.com | vmware.com:772044a3-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
| moxxxxxx@vmware.com | Mike | Oxxxxxx | moxxxxxx@vmware.com | vmware.com:9b33c87f-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
| tjxxxxx@vmware.com | Tim | Jxxxxx | tjxxxxx@vmware.com | vmware.com:a2267e8e-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
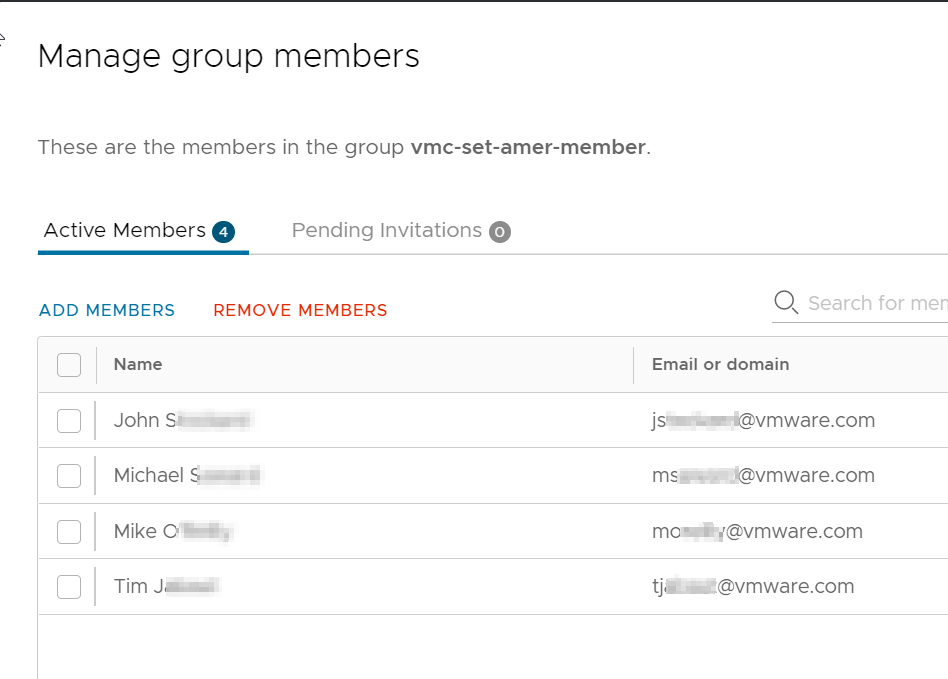
+----------------------+------------+-----------+----------------------+-------------------------------------------------+Here is what the group members look like in the CSP UI.
show-csp-group-diff
This command lets you compare user roles against the roles in an existing group, showing you the differences.
What I needed to do was create a group with a specific set of roles, then look at the users who were already directly assigned roles to determine the impact. Did somebody have a specific set of permissions that they need, which I am now going to override by putting them into a group?
I have the vmc-set-amer-member group configured the way I want it, I use show-csp-groups to get the group ID. Then I run the show-csp-group-diff without any arguments
C:\git\Flings\python-client-for-vmware-cloud-on-aws [master ≡ +0 ~1 -0 !]> python .\pyVMC.py show-csp-group-diff
Usage: show-csp-group-diff [groupID] [showall|skipmembers|skipowners]I see I need to pass the command a groupID, and then I have 3 choices for the second argument:
- showall – Show every user in the org
- skipmembers – Do not show org members – show only org owners
- skipowners – Do not show org owners – show only org members
I pass the command the org-members group and tell it to skip org owners.
C:\git\Flings\python-client-for-vmware-cloud-on-aws [master ≡ +0 ~1 -0 !]> python .\pyVMC.py show-csp-group-diff 3d6f43a8-xxxx-xxxx-xxxx-xxxxxxxxxxxx skipowners
Skipping owners…
Group role list:
['vrni:admin', 'vrni:user', 'log-intelligence:admin', 'log-intelligence:user', 'automationservice:user', 'automationservice:cloud_admin', 'CodeStream:developer', 'CodeStream:viewer', 'nsx:cloud_auditor', 'vmc-user:restricted', 'nsx:cloud_admin', 'discovery:user', 'hcx:admin', 'catalog:admin', 'catalog:user', 'vcdr:administrator', 'srv-marketplace:marketplaceuser']
axxxxxxxxx@vmware.com (1 of 130)
Member: True, Owner: False
User role list:
['srv-marketplace:marketplaceuser', 'automationservice:user', 'automationservice:cloud_admin', 'hcx:admin', 'catalog:admin', 'catalog:user', 'discovery:user', 'log-intelligence:admin', 'log-intelligence:user', 'vrni:admin', 'vrni:user', 'vmc-user:full', 'nsx:cloud_auditor', 'nsx:cloud_admin']
Role Differences:
{'iterable_item_added': {'root[11]': 'vmc-user:full'}, 'iterable_item_removed': {'root[6]': 'CodeStream:developer', 'root[7]': 'CodeStream:viewer', 'root[9]': 'vmc-user:restricted', 'root[15]': 'vcdr:administrator'}}Focusing on the role differences output – this user has a role called vmc-user:full that is not part of the group, and the group has CodeStream:developer, CodeStream:viewer, vmc-user:restricted, and vcdr:administrator roles, which the user would inherit if we add them to the group.
You have to look at users one-by-one, but it’s easier to view this output to help figure out who gets what role. The output is raw and display improvements could be made in future versions, but it does the job for now.
Here is an example of a user with no differences – their roles are an exact match for the group.
jsxxxxxxx@vmware.com (49 of 130)
Member: True, Owner: False
User role list:
['srv-marketplace:marketplaceuser', 'nsx:cloud_auditor', 'vmc-user:restricted', 'nsx:cloud_admin', 'automationservice:user', 'automationservice:cloud_admin', 'hcx:admin', 'CodeStream:developer', 'CodeStream:viewer', 'log-intelligence:admin', 'log-intelligence:user', 'vcdr:administrator', 'catalog:admin', 'catalog:user', 'discovery:user', 'vrni:admin', 'vrni:user']
Role Differences:
{}There is no equivalent function in the CSP UI for this command – you would have to manually look at each user.
show-csp-org-users
This command lets you search your org for users. For testing purposes I have added myself to my org 3 times with 3 separate email addresses. Each of the email addresses contains the string ‘pk’ in it – a search on that string returns all 3 of my user accounts.
C:\git\Flings\python-client-for-vmware-cloud-on-aws [master ≡ +0 ~1 -0 !]> python .\pyVMC.py show-csp-org-users pk
+-----------------------+------------+-----------+-----------------------+-------------------------------------------------+
| Username | First Name | Last Name | Email | userId |
+-----------------------+------------+-----------+-----------------------+-------------------------------------------------+
| pkxxxxx@xxxxxxxxx.com | Patrick | Kremer | pkxxxxx@xxxxxxxxx.com | vmwareid:ffb9490d-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
| pk@xxxxxxxxx.com | Patrick | Kremer | pk@xxxxxxxxx.com | vmwareid:9f45c06d-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
| pkxxxxx@yyyyyy.com | Patrick | Kremer | pkxxxxx@yyyyyy.com | vmware.com:ccafda0e-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
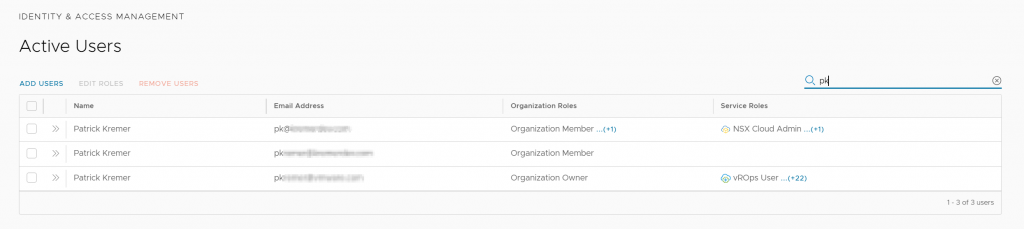
+-----------------------+------------+-----------+-----------------------+-------------------------------------------------+Here is what the user search looks like in the CSP UI.
add-users-to-csp-group
This command lets you add users to a group. After retrieving a group ID from show-csp-groups, you pass it with a comma-delimited list of email addresses to add them to the group.
C:\git\Flings\python-client-for-vmware-cloud-on-aws [master ≡ +0 ~1 -0 !]> python .\pyVMC.py add-users-to-csp-group 3d6f43a8-xxxx-xxxx-xxxx-xxxxxxxxxxxx pk@xxxxxxxxx.com,pkxxxxx@xxxxxxxxx.com
Added: ['pkxxxxxx@xxxxxxxxx.com', 'pk@xxxxxxxxx.com']
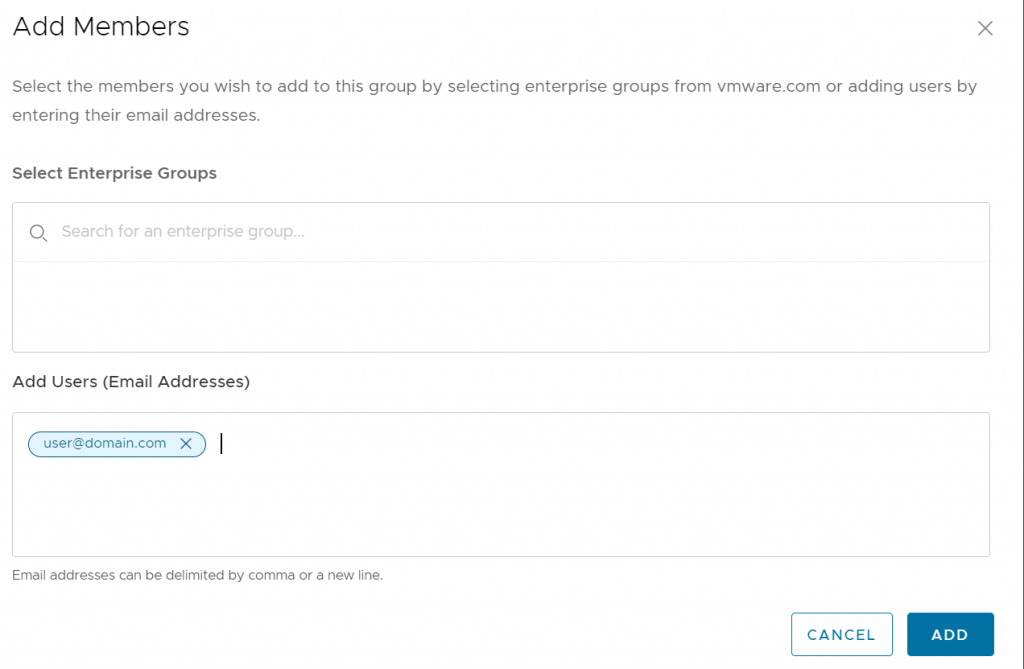
Failed: []Here is what adding a user to a group looks like in the CSP UI.
That’s all for this post. In Part II, we look at more user management commands.

Python Client for VMC on AWS - Part II - More User Management -
[…] Part I of this series, we examined some of the user management functions in v1.4 of PyVMC. In this post, […]