Many thanks to the awesome Nico Vibert for showing me this trick.
I’ve been writing code against the VMC API and have been having problems debugging some of the calls.
For this example, we will work with the NSX-T services API. Services define ports and protocols i.e. HTTP runs on TCP/80. First we go to Developer Center, pick my SDDC out of the dropdown, then go to the NSX VMC Policy API.
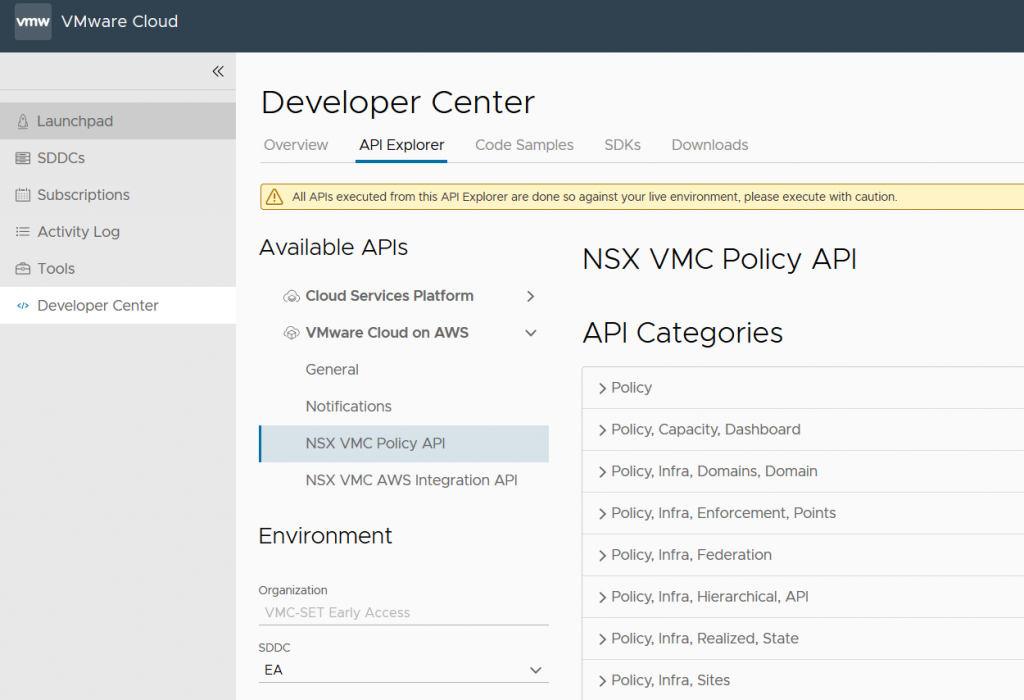
Find the Policy,Inventory,Services objects.

Execute the GET request for /infra/services
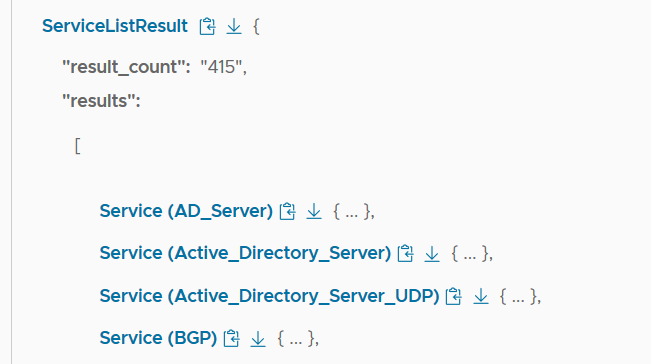
We get a ServiceListResult, which we can click on and see all of the services defined in our SDDC (screenshot truncated).
API explorer makes it easy to play with the API and get it working. But when you’re writing code against the API in a programming language, it can be very difficult to figure out where your mistakes are when you can’t successfully call the API programmatically.
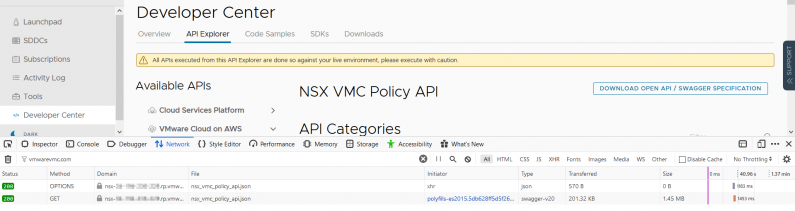
Firefox has a Web Developer tool with awesome web debugging tools. You can enable them as shown below. For working with APIs, we want the Network debugger.
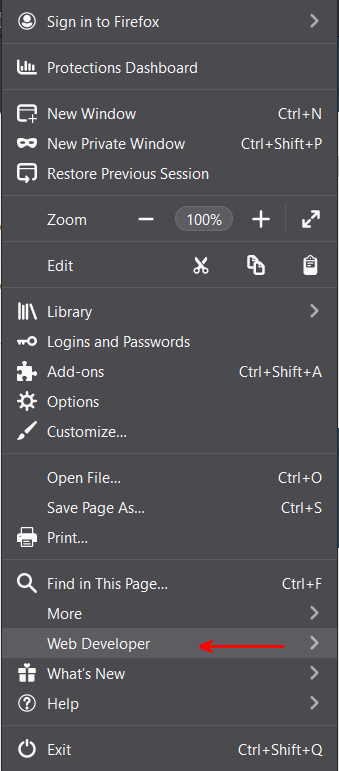
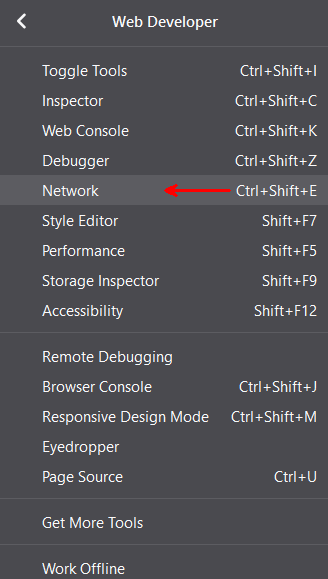
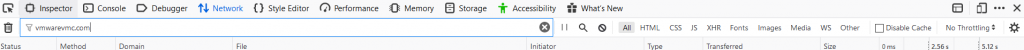
This opens up a debugging window at the bottom of Firefox. We can do a filter by typing ‘vmwarevmc.com’ in the filter box. Now only URLS with the VMC API vmwarevmc.com in it will show up.
When we execute the GET request, it shows up below.
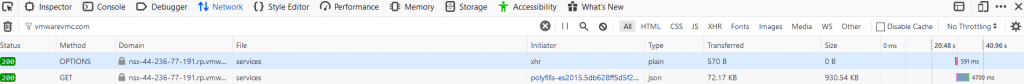
We can click on the request and see the entire API call – the GET request, URL, headers, Response, etc. If we were doing a PUT request, we would also see the JSON payload in the Request tab.
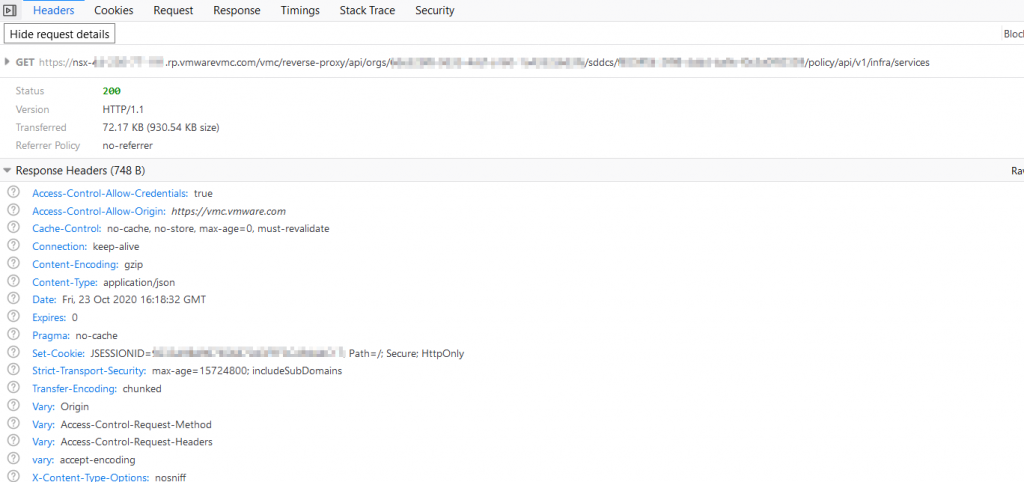

Using this technique makes it significantly easier to troubleshoot your code. It also highlighted something that I understood incorrectly – I had a mental image of API explorer executing calls on a server running the cloud services portal somewhere. That’s not what’s happening – your own browser is making the API calls. You can click anywhere in the VMC on AWS UI and see exactly what’s happening under the covers. This is not limited to the API explorer, you can perform any operation in the UI and see the underlying API call and payload using this technique.